EdgeRouter routers with EdgeOS firmware version 2.0.9 and later support long passwords and can be used to establish a connection to our servers using the OpenVPN protocol. If you are using an older version of the firmware, please update it before following this guide. Instructions on how to update the router firmware can be found on the official Ubiquiti website here.
Here are the instructions on how to set up an OpenVPN connection to NordVPN servers on EdgeRouter via SSH:
1. Create a new file on your computer and call it nordvpnauth.txt. Open it and type in your NordVPN service username in the first line and NordVPN service password in the second line:
username
password
You can find your NordVPN service credentials at the Nord Account. Copy the credentials using the buttons on the right.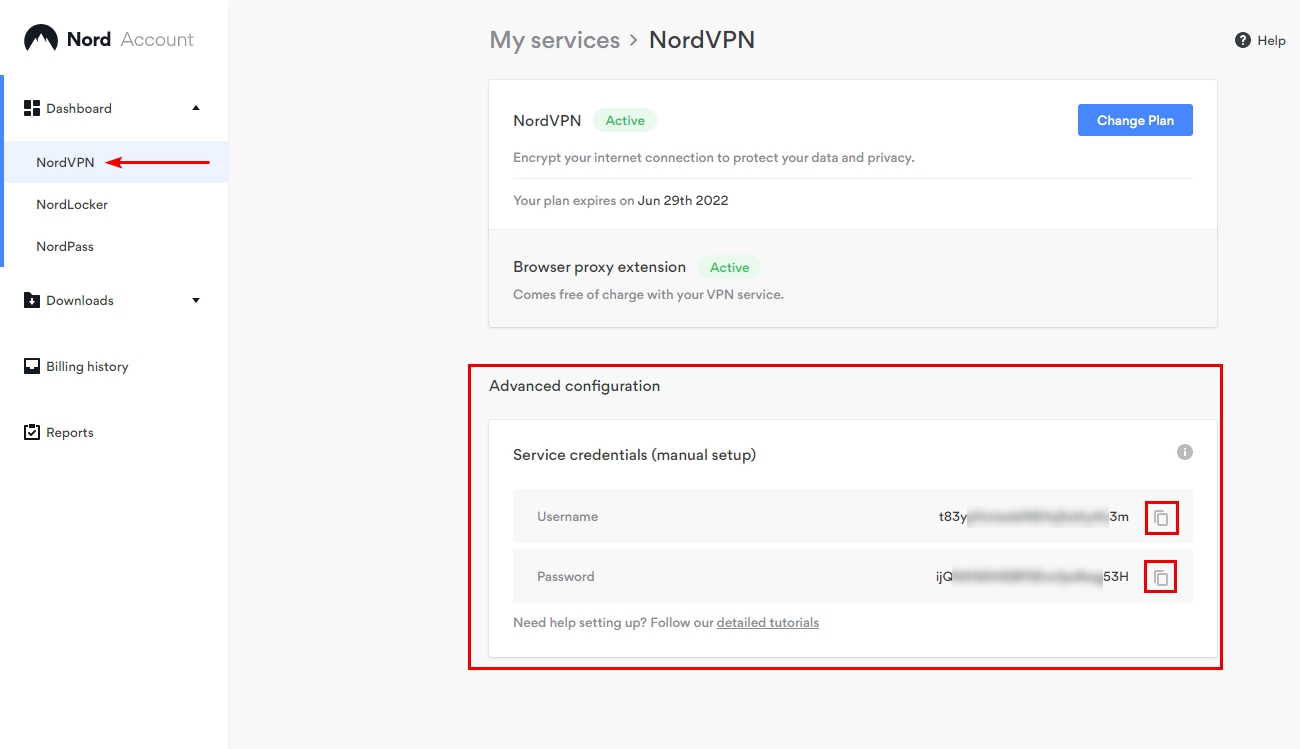
2. Go to our recommended server utility here. In the server picker, click on the Show available protocols highlight. Then download a server configuration file, and it will have all the information needed for this guide.

3. After downloading the server configuration, please open it, for example, de978.nordvpn.com.udp1194.ovpn, and modify it. Change this line:
auth-user-pass
into
auth-user-pass /config/openvpn/nordvpnauth.txt
And add an additional line
route-nopull
then save the file. Your configured file should look like this:
|
client remote-cert-tls server auth-user-pass /config/openvpn/nordvpnauth.txt verb 3 |
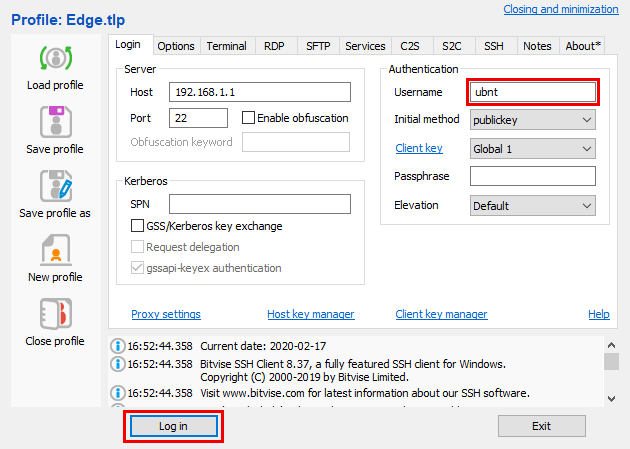
4. Now access your EdgeMax router via SSH. For UNIX-like machines:
ssh ubnt@routersIPaddress
You will be asked to enter the password of your EdgeRouter.
For Windows devices, download this app:https://www.bitvise.com/ssh-client-downlo
5. Then perform these commands:
sudo -i
cd /config/
mkdir openvpn
chmod 770 openvpn
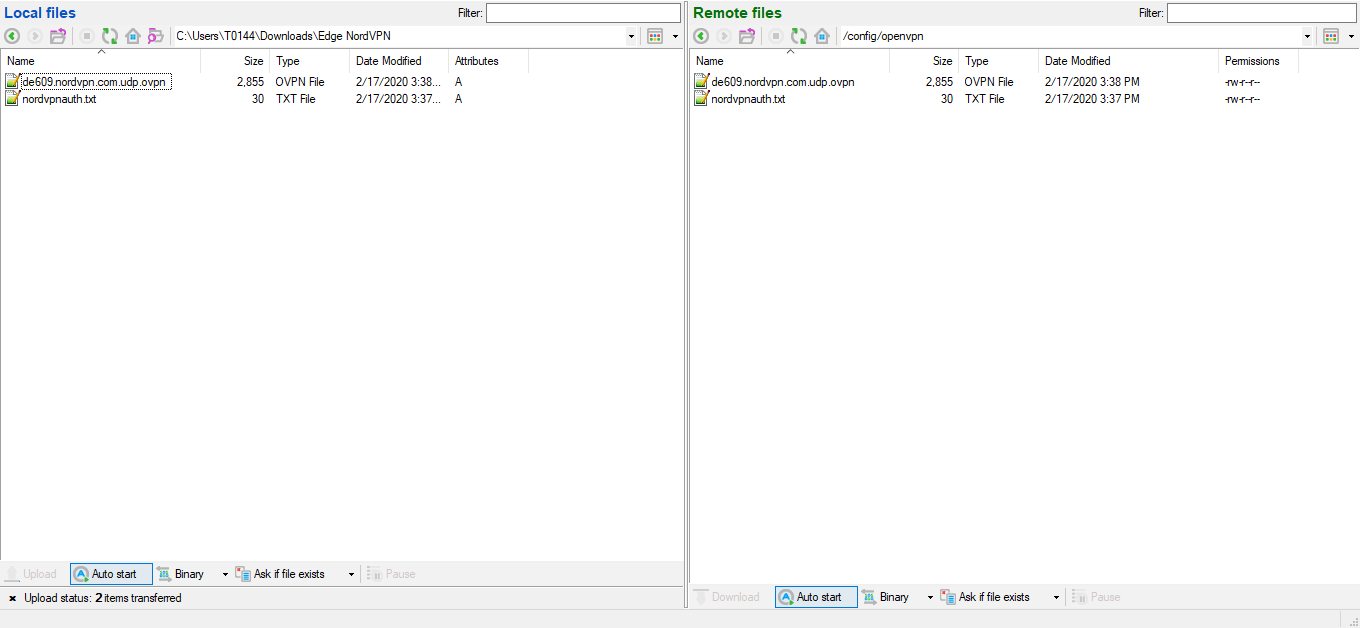
6. If you're using Linux, disconnect from SSH and then copy the created files nordvpnauth.txt and downloadeded .ovpn file (in this case de978.nordvpn.com.udp.ovpn into your EdgeMax router's /config/openvpn directory via SCP:
scp nordvpnauth.txt ubnt@routersIPaddress:/config/openvpn
scp de978.nordvpn.com.udp1194.ovpn ubnt@routersIPaddress:/config/openvpn
In order to copy these files into the EdgeRouter while using Windows, upload them via SFTP. The default port for the SFTP connection is 22:
7. SSH again into your router and run the following commands (adjust some of the lines according to your network and file names):
configure
set interfaces openvpn vtun0 config-file /config/openvpn/de978.nordvpn.com.udp.ovpn
set interfaces openvpn vtun0 description 'OpenVPN VPN tunnel'
commit
set service nat rule 5000 description 'OpenVPN Clients'
set service nat rule 5000 log disable
set service nat rule 5000 outbound-interface vtun0
set service nat rule 5000 source address 192.168.1.0/24
set service nat rule 5000 type masquerade
commit
set protocols static table 1 interface-route 0.0.0.0/0 next-hop-interface vtun0
set firewall modify SOURCE_ROUTE rule 10 description 'traffic from 192.168.1.0/24 to vtun0'
set firewall modify SOURCE_ROUTE rule 10 source address 192.168.1.0/24
set firewall modify SOURCE_ROUTE rule 10 modify table 1
set interfaces ethernet eth1 firewall in modify SOURCE_ROUTE
commit
save
Note: in the last command, it can also be ethernet eth2 depending on which slot is used for the LAN cable, or switch switch0 if you are using a switch interface.
If you are using a different subnet or wish to use only for specific devices, modify 192.168.1.0/24 on all lines to your values.
8. To check the connection log you can type in:
run show log
And scroll down till you see Initialization Sequence Completed. That means your router is successfully connected to our service. You can also check this website to check if you are connected
Additional notes:
- To disable a VPN, use the following commands:
configure
set interfaces openvpn vtun0 disable
commit
save
- To re-enable VPN back, use the following commands:
configure
delete interfaces openvpn vtun0 disable
commit
save
- To change a VPN server, simply upload a new file to your router (step 9) and use the following commands:
configure
set interfaces openvpn vtun0 config-file /config/openvpn/new_file.ovpn
commit
save